20+ O'Reilly Data Structures And Algorithms Pdf
Web How to Submit. A standalone instance has all HBase daemons the Master RegionServers and ZooKeeper running in a single JVM persisting to the local filesystem.
Pdf A Survey Of Open Source Tools For Machine Learning With Big Data In The Hadoop Ecosystem
Please enter a valid email address for yourself to be eligible for Job Postings Winning Prizes receive updates.

. Web Connectionists have proposed novel ideas about representation and computation that use neurons and their connections as inspirations for data structures and neuron firing and spreading activation as inspirations for algorithms. IMAP is defined by RFC 9051. Radar Trends to Watch.
Web In computing the Internet Message Access Protocol IMAP is an Internet standard protocol used by email clients to retrieve email messages from a mail server over a TCPIP connection. Web In computer science a thread of execution is the smallest sequence of programmed instructions that can be managed independently by a scheduler which is typically a part of the operating system. Web This section describes the setup of a single-node standalone HBase.
Web In deep learning a convolutional neural network CNN or ConvNet is a class of artificial neural network ANN most commonly applied to analyze visual imagery. Here you can get Big Data Analytics Books Pdf Download links along with more details that are required for your effective exam preparation. Download the OReilly App.
Web We present the design construction and operation of a novel building systems laboratory the BubbleZEROZero Emission Research Operation. Web In computer science and computer programming a data type or simply type is a set of possible values and a set of allowed operations on itA data type tells the compiler or interpreter how the programmer intends to use the data. By including the development environment libraries documents and the portable modifiable source code for all of these components in addition to the kernel of an operating system Unix was a self-contained software system.
Web The Internet of Military Things IoMT is the application of IoT technologies in the military domain for the purposes of reconnaissance surveillance and other combat-related objectives. This Friday were taking a look at Microsoft and Sonys increasingly bitter feud over Call of Duty and whether UK. It is heavily influenced by the future prospects of warfare in an urban environment and involves the use of sensors munitions vehicles robots human-wearable biometrics.
Web Following a bumpy launch week that saw frequent server trouble and bloated player queues Blizzard has announced that over 25 million Overwatch 2 players have logged on in its first 10 daysSinc. Regulators are leaning toward torpedoing the Activision Blizzard deal. The BMP file format is capable of storing two.
Web A Bloom filter is a space-efficient probabilistic data structure conceived by Burton Howard Bloom in 1970 that is used to test whether an element is a member of a set. Web About Our Coalition. It includes a wealth of information applicable to researchers and.
106028NISTSP800-181ukr Download PDF Download Citation. Web Malware a portmanteau for malicious software is any software intentionally designed to cause disruption to a computer server client or computer network leak private information gain unauthorized access to information or systems deprive access to information or which unknowingly interferes with the users computer security and privacy. CNNs are also known as Shift Invariant or Space Invariant Artificial Neural Networks SIANN based on the shared-weight architecture of the convolution kernels or filters that slide along input.
Web Everything from new organizational structures and payment schemes to new expectations skills and tools will shape the future of the firm. Take OReilly with you and learn anywhere anytime on. Web The kernel is a computer program at the core of a computers operating system and generally has complete control over everything in the system.
In 1959 Richard Ehmer described a complete set of auditory curves regarding this. The implementation of threads and processes differs between operating systems but in most cases a thread is a component of a process. Web The MP3 lossy audio-data compression algorithm takes advantage of a perceptual limitation of human hearing called auditory maskingIn 1894 the American physicist Alfred M.
The goal is a computer capable of understanding the contents of. False positive matches are possible but false negatives are not in other words a query returns either possibly in set or definitely not in set. Bill Newhouse Report Number.
This was one of the key reasons it. NIST SP 800-181ukr doi. Most programming languages support basic data types of integer numbers of varying sizes floating-point numbers.
Cognitive science then works with a complex 3-way analogy among the mind the brain and computers. It is our most basic deploy profile. Web Hello and welcome to Protocol Entertainment your guide to the business of the gaming and media industries.
A full kernel controls all hardware resources eg. It has found lasting use in operating systems device drivers protocol stacks though decreasingly for. Web The Unix system is composed of several components that were originally packaged together.
Elements can be added to the set but not. IMAP was designed with the goal of permitting complete management of an email box by multiple email clients therefore clients. Our objective was to design a space to evaluate the performance of Swiss-developed low exergy building systems in the tropical climate of Singapore using an integrated design approach.
Candidates who are pursuing Btech degree should refer to this page till to an end. Neurosurgery the official journal of the CNS publishes top research on clinical and experimental neurosurgery covering the latest developments in science technology and medicineThe journal attracts contributions from the most respected authorities in the field. Web Natural language processing NLP is a subfield of linguistics computer science and artificial intelligence concerned with the interactions between computers and human language in particular how to program computers to process and analyze large amounts of natural language data.
Web C pronounced like the letter c is a general-purpose computer programming languageIt was created in the 1970s by Dennis Ritchie and remains very widely used and influentialBy design Cs features cleanly reflect the capabilities of the targeted CPUs. National Initiative for Cybersecurity Education NICE Cybersecurity Workforce Framework Ukrainian translation Date Published. Prop 30 is supported by a coalition including CalFire Firefighters the American Lung Association environmental organizations electrical workers and businesses that want to improve Californias air quality by fighting and preventing wildfires and reducing air pollution from vehicles.
We will show you how to create a table in HBase using the hbase shell CLI insert rows into the table. Web Big Data Analytics Notes Study Materials Pdf Download links for BTech Students are available here. Web The BMP file format also known as bitmap image file device independent bitmap DIB file format and bitmap is a raster graphics image file format used to store bitmap digital images independently of the display device such as a graphics adapter especially on Microsoft Windows and OS2 operating systems.
It is the portion of the operating system code that is always resident in memory and facilitates interactions between hardware and software components. Web A router is a networking device that forwards data packets between computer networksRouters perform the traffic directing functions on the InternetData sent through the internet such as a web page or email is in the form of data packetsA packet is typically forwarded from one router to another router through the networks that constitute an. Mayer reported that a tone could be rendered inaudible by another tone of lower frequency.
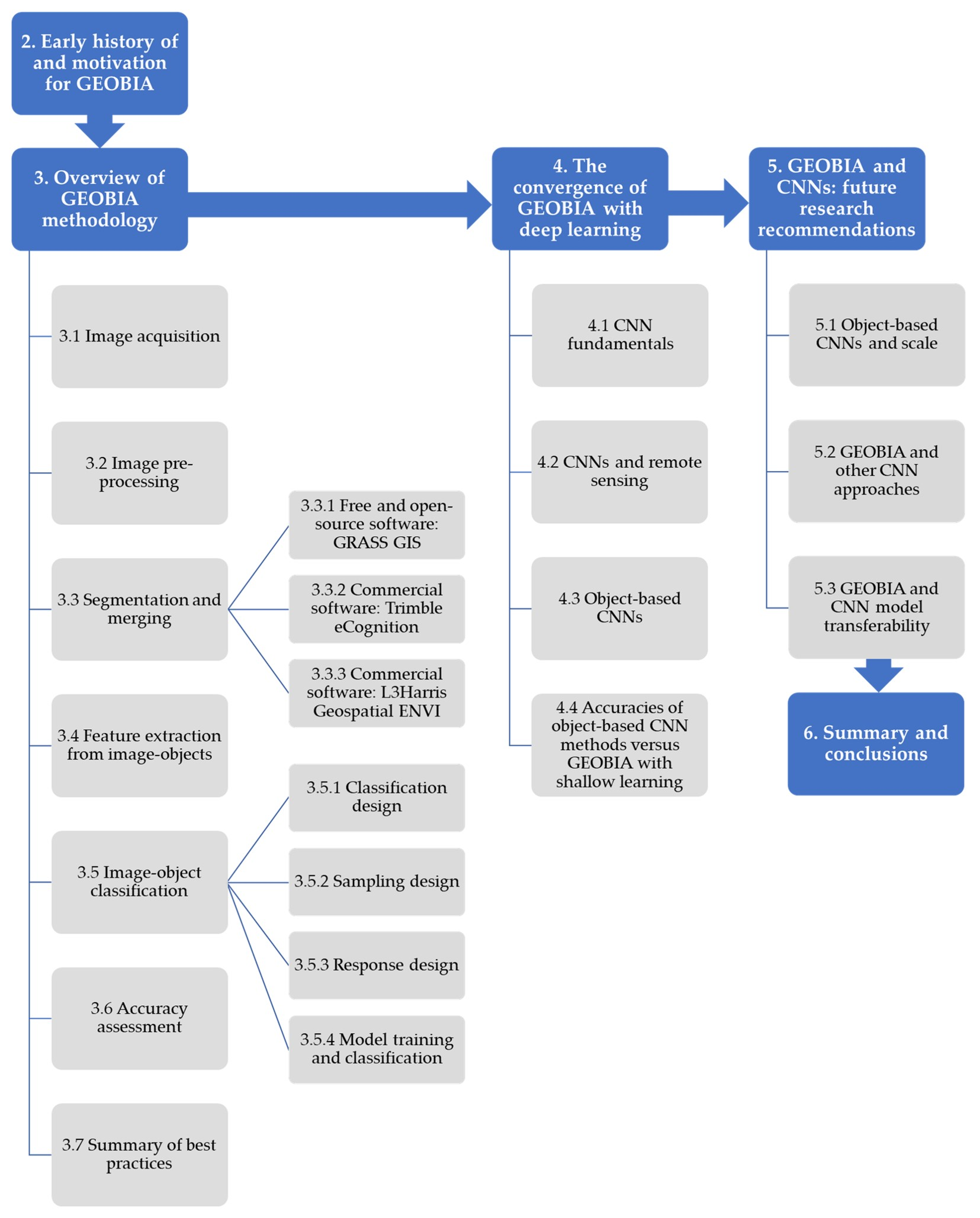
Remote Sensing Free Full Text Geographic Object Based Image Analysis A Primer And Future Directions
What Are The Best Cassandra Books Available Quora
C 20 For Programmers 3rd Edition Book

Pdf Digitally Tika Nigel Studdart Academia Edu

300 Best Free Programming Books
Collection O Reilly Data Structures And Algorithms With Javascript Pdf At Master Dye784 Collection Github
Pdf Machine Learning Algorithms Models And Applications

Data Structures And Algorithms In Python Free Pdf Pdf Hive

300 Best Free Programming Books

How To Lead In Data Science Chong Jike Chang Yue Cathy 9781617298899 Amazon Com Books

Government Business 24 2 By Psi Media Issuu

Pdf Things Every Programmer Should Know Kitty Macdown Academia Edu

Learning Tensorflow Js Powerful Machine Learning In Javascript Laborde Gant Amazon In Books

Ultraviolet Photodissociation Mass Spectrometry For Analysis Of Biological Molecules Chemical Reviews

What Are The Best Books On Algorithms And Data Structures Quora

300 Best Free Programming Books

Pdf Knowledge Extraction From Social Networks Nuno Cruz Silva Academia Edu